Eliminate Risk of Failure with Eccouncil ECSAv10 Exam Dumps
Schedule your time wisely to provide yourself sufficient time each day to prepare for the Eccouncil ECSAv10 exam. Make time each day to study in a quiet place, as you'll need to thoroughly cover the material for the Certified Security Analyst (ECSA) v10 exam. Our actual EC-Council Certified Security Analyst exam dumps help you in your preparation. Prepare for the Eccouncil ECSAv10 exam with our ECSAv10 dumps every day if you want to succeed on your first try.
All Study Materials
Instant Downloads
24/7 costomer support
Satisfaction Guaranteed
Mason is footprinting an organization to gather competitive intelligence. He visits the company's website for contact information and telephone numbers but does not find any. He knows the entire staff directory was listed on their website 12 months. How can he find the directory?
You work as a penetration tester for Hammond Security Consultants. You are currently working on a contractfor the state government of Californi
a. Your next step is to initiate a DoS attack on their network. Why wouldyou want to initiate a DoS attack on a system you are testing?
What is the target host IP in the following command?
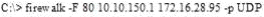
An attacker injects malicious query strings in user input fields to bypass web service authentication mechanisms and to access back-end databases. Which of the following attacks is this?
Transmission Control Protocol (TCP) is a connection-oriented four layer protocol. It is responsible for breaking messages into segments, re-assembling them at the destination station, and re-sending. Which one of the following protocols does not use the TCP?
Are You Looking for More Updated and Actual Eccouncil ECSAv10 Exam Questions?
If you want a more premium set of actual Eccouncil ECSAv10 Exam Questions then you can get them at the most affordable price. Premium EC-Council Certified Security Analyst exam questions are based on the official syllabus of the Eccouncil ECSAv10 exam. They also have a high probability of coming up in the actual Certified Security Analyst (ECSA) v10 exam.
You will also get free updates for 90 days with our premium Eccouncil ECSAv10 exam. If there is a change in the syllabus of Eccouncil ECSAv10 exam our subject matter experts always update it accordingly.
