Eliminate Risk of Failure with Cisco 350-201 Exam Dumps
Schedule your time wisely to provide yourself sufficient time each day to prepare for the Cisco 350-201 exam. Make time each day to study in a quiet place, as you'll need to thoroughly cover the material for the Performing CyberOps Using Core Security Technologies exam. Our actual Cisco Certified CyberOps Professional exam dumps help you in your preparation. Prepare for the Cisco 350-201 exam with our 350-201 dumps every day if you want to succeed on your first try.
All Study Materials
Instant Downloads
24/7 costomer support
Satisfaction Guaranteed
Refer to the exhibit.
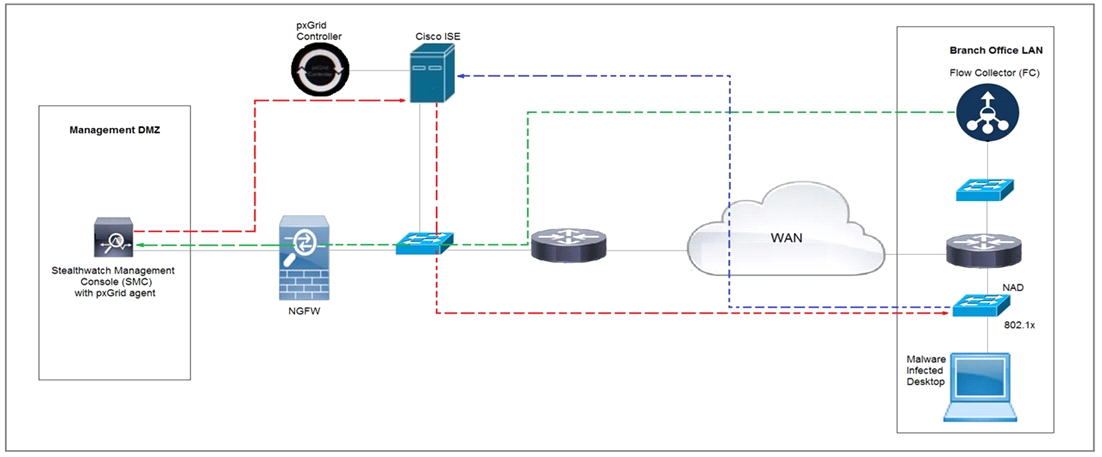
Rapid Threat Containment using Cisco Secure Network Analytics (Stealthwatch) and ISE detects the threat of malware-infected 802.1x authenticated endpoints and places that endpoint into a quarantine VLAN using Adaptive Network Control policy. Which method was used to signal ISE to quarantine the endpoints?
Refer to the exhibit.
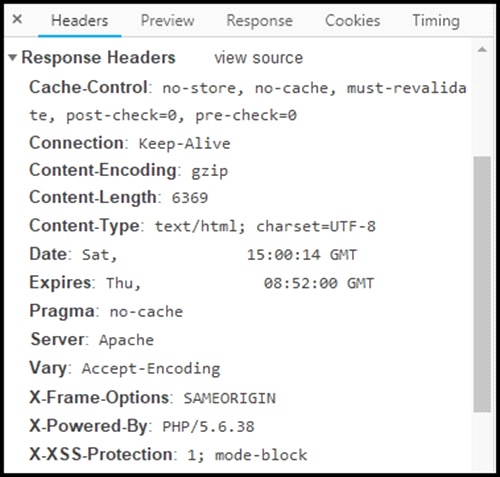
Where are the browser page rendering permissions displayed?
After a recent malware incident, the forensic investigator is gathering details to identify the breach and causes. The investigator has isolated the affected workstation. What is the next step that should be taken in this investigation?
An analyst received multiple alerts on the SIEM console of users that are navigating to malicious URLs. The analyst needs to automate the task of receiving alerts and processing the data for further investigations. Three variables are available from the SIEM console to include in an automation script: console_ip, api_token, and reference_set_name. What must be added to this script to receive a successful HTTP response?
#!/usr/bin/python import sys import requests
What is the difference between process orchestration and automation?
Are You Looking for More Updated and Actual Cisco 350-201 Exam Questions?
If you want a more premium set of actual Cisco 350-201 Exam Questions then you can get them at the most affordable price. Premium Cisco Certified CyberOps Professional exam questions are based on the official syllabus of the Cisco 350-201 exam. They also have a high probability of coming up in the actual Performing CyberOps Using Core Security Technologies exam.
You will also get free updates for 90 days with our premium Cisco 350-201 exam. If there is a change in the syllabus of Cisco 350-201 exam our subject matter experts always update it accordingly.
